
Checklist to Rock iOS App Testing. Part I
Any self-respecting client, ordering testing of iOS platform mobile application, wants to get a stable, reliable, polished software in the end. Although, sometimes the customer doesn’t completely understand that app’s testing isn’t carried out strictly within the product itself. It is important to check out other aspects outside the application, which could have a significant impact on result’s quality.
Therefore, to build rapport and trust between testers and customers and save some time on explanations, we suggest these top 7 must have checkpoints crucial for iOS:
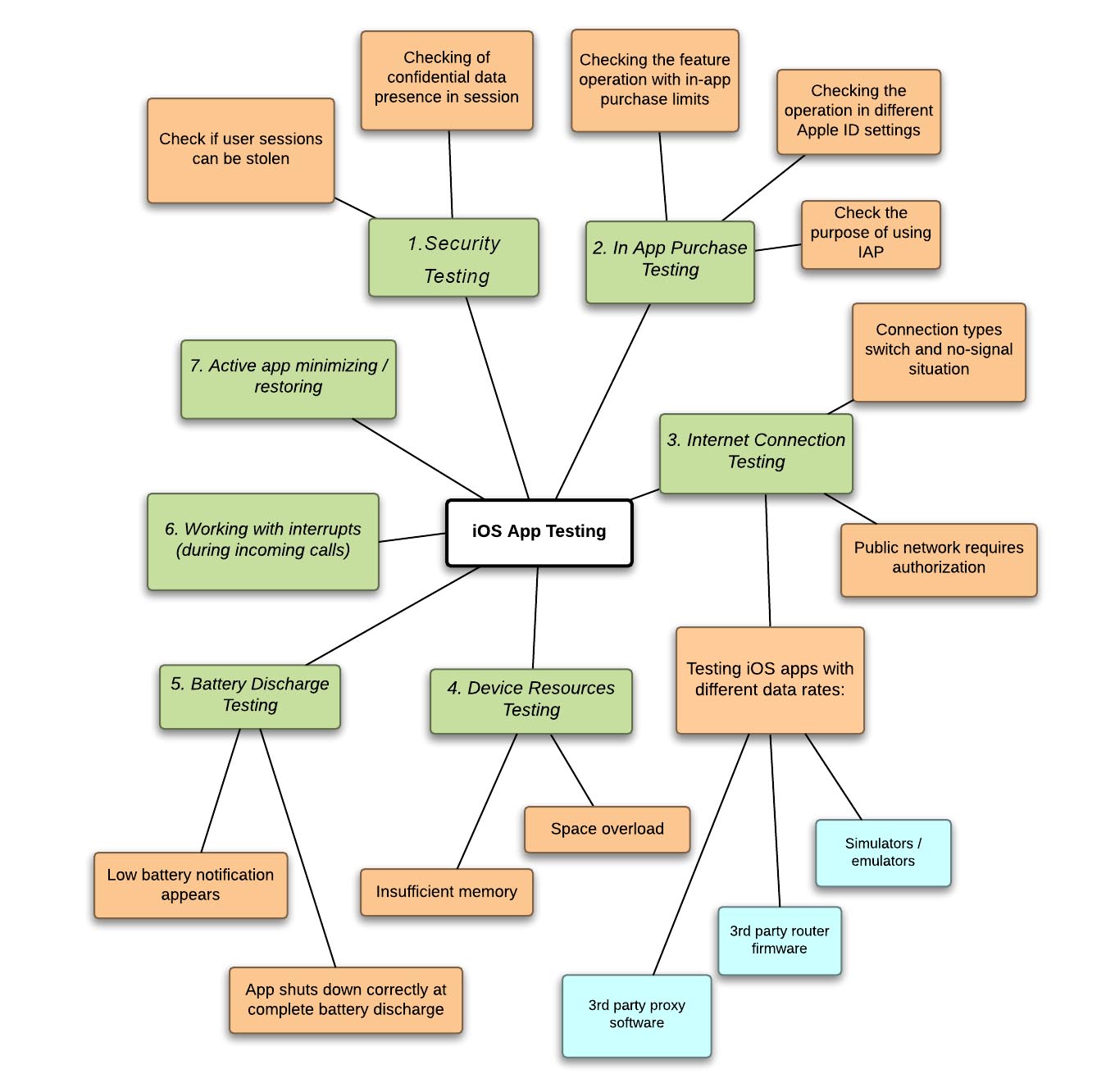
#1. Security Testing.
Each app user wants his personal data safe and secure. To make this wish come true, we provide the full security check (pentesting). One of the tests is to verify if any network sniffers could intercept the incoming or outgoing data. This check-up is very important for corporate apps, banking software and applications running on the https protocol, because Wi-Fi data transfer creates a certain degree of vulnerability to MITM attacks ("man in the middle", in other words). Testing the iPhone app with FireSheep, we check if user sessions could be stolen, and if sessions contain any confidential data.
#2. In-App Purchase Test.
It should be noted, that during testing In-App Purchase feature in iOS app, tester must pay attention to prices. Every content’s cost in the app should match with what user sees. Also, don’t miss the option to restore the purchases made by the user, after updating the program.
- Check the feature operation with given constraints:
After installing the in-app purchase limits, user expects to be protected, but if the restriction is not applied on your application and, for example, a child, a younger brother or sister by negligently commit is not very necessary purchase, the user will be very distressed. Therefore, when setting limits in the settings should appear warning when trying to implement In-App Purchase.
- Check the feature operation in different settings of Apple ID:
When logging in with another Apple ID, previous ID purchase information isn’t stored. Thereby, user data remains confidential. Don’t forget that if the user doesn’t change his Apple ID, exits the app and re-enters, then purchase data shall be stored.
- Check the purpose of using IAP. Simple rules:
1. Applications that use IAP to purchase "credits" or other currencies are obliged to ensure the use of these "credits" inside themselves.
2. In case of a limited shelf life for "credits" and other currencies app doesn’t use IAP to buy them.
3. Content subscription by IAP must be provided to the user on any IOS-devices he owns with the duration not less than 30 days.

#3. Different Types of Internet Connection:
1. Cellular: 2G, 2.5G, 3G, 4G
2. Wi-Fi
3. Mi-Fi - the transfer point of internet received by cellular.
These days almost all phones use modern technology to transmit mobile data traffic. The device can access the connection type (2G / 3G / 4G) through settings. It stands to mention that the connection constraints regard not only mobile data traffic, but also Wi-Fi.
- There are 3 methods of testing iOS apps with different data rates:
1. The use of simulators / emulators;
2. 3rd party router firmware;
3. 3rd party software (of different proxies).
- Connection types switch and no-signal:
Swipe up from the bottom of Home Screen, and tap theAirplane Mode icon or turn off Wi-Fi. Shut down or restart the access point, thereby disabling mobile data traffic. Typically, the OS settings allow switching automatically from cellular to Wi-Fi and vice versa if the stronger source of signal is available. For example:
1. App switches on cellular (2G / 2.5G / 3G / 4G), when you turn off Wi-Fi;
2. Automatic switch to Wi-Fi when it is on and connected to the correct network.
- “Public network requiring authorization” version check:
While testing the application networking, don’t forget about public access pointsthat require authorization.
Connecting to a network with no internet can cause crashes, because the queries cannot reach the destination, and due to received responses mismatch with the expected ones.
Here are some widespread cases with required authorization:
1. Web-authentication, occurring immediately after the Wi-Fi connection. This type of connection doesn’t provide access to services different from the primary.
2. LAN router connecting through binding to MAC-address of the device. This type of connection allows you to connect to Wi-Fi, but restricts access to internet use.
3. Transfer to web authentication when sending the request to any public address.
For more information on helpful iOS testing tips, wait for the second part of the article. You’ll know how to prevent your users from deleting the game you developed, what is really iPhone for and how app should deal with battery discharge.